
Modernizing Legacy Apps for True Cloud Scalability
As businesses grow, systems that once worked well begin to show strain not because they were built poorly, but because they were never designed for modern scale. Legacy scheduling and application stacks often mix tightly coupled services, local file dependencies, and operational workflows that make scaling complex, brittle, or costly.

Cloud Infrastructure Designed to Scale
In modern cloud deployments, companies often find themselves balancing cost, performance, and flexibility while they build or re-platform infrastructure. Choosing the right architecture early can determine how well systems handle scale, user growth, and operational complexity long before edge cases turn into bottlenecks.

Keeping Your IoT Devices Online and Reliable
In today’s connected world, IoT devices are essential for businesses, developers, and tech enthusiasts. Yet many struggle to keep their devices online and communicating properly with platforms like AWS IoT Core. Often, the problem isn’t the device itself, it’s small, avoidable mistakes in setup, code, or configuration that block proper connectivity.

How Custom Labeling with AutoML Transforms Image Rekognition
Image recognition has become a critical capability across industries from retail and manufacturing to healthcare and logistics. Yet many businesses struggle to extract real value from AI-powered vision systems. The issue is rarely the model itself. More often, it’s the data.
Generic image recognition models can identify common objects, but real-world business use cases demand precision. That’s where custom labeling combined with AutoML changes everything.

How to Strengthen Cloud Security Through the AWS Well-Architected Framework
In today’s cloud-driven world, businesses rely heavily on digital systems. But even strong infrastructure can be undermined by basic security gaps like weak or reused passwords or old keys. What starts as a small vulnerability can quickly expose sensitive data, customer information, or even entire cloud environments.
At SoftStackers, we help companies eliminate these risks using the AWS Well-Architected Framework (WAF). By following AWS best practices, we design systems that are secure, resilient, and scalable from day one.

Stability Starts With Observability
For many growing organizations, cloud issues don't start with outages; they start with blind spots.
When systems slow down, APIs time out, and customers experience friction, teams struggle to answer critical questions: What is failing? Why now? And what changed? By the time teams gather logs and test assumptions, the problem has already escalated to impact the business.

How WorldClass IT Departments Handle Losing Key Employees
IT departments in most businesses often face significant challenges when a core IT staff member departs, leading to immediate consequences like operational disruption and security vulnerabilities. SoftStackers helps address these common pain points by leveraging AWS solutions and our own methods of support delivery where we are an extension of your team.

We don't charge for support. Only value.
In any business, controlling every dollar is essential. Many service providers utilize flat rates, retainers, or bundled packages, which often include services a company might not actually require.
At SoftStackers, we recognized that our customers needed a more flexible, value based, on-demand approach, just like their AWS cloud costs.

How Small and Mid-Sized Businesses Break Silos and Unlock Insights with AI
Data silos pose a significant obstacle to business growth, regardless of company size. When information is fragmented across departments, effective collaboration among sales, inventory, operations, and finance teams becomes challenging, leading to delayed decisions and missed opportunities. While large enterprises often utilize sophisticated systems to manage this issue, mid-market and small businesses face similar challenges, albeit on a smaller scale. Fortunately, these obstacles are no longer insurmountable.

How Startups Can Overcome the 3 Biggest AI Myths
AI often seems inaccessible to many startups perceived as too expensive, intricate, or premature. However, the true obstacles are not technical; they are misconceptions.
These myths suggest that AI is exclusively for large enterprises, that a flawless data warehouse is a prerequisite, or that a team of data scientists is essential for its implementation.

Protect Your Self Against Cloudflare Disruptions
Recent Cloudflare outages have made one thing clear: even the most trusted global edge networks are not immune to downtime.
When Cloudflare experiences a disruption, businesses that depend on it for DNS, CDN delivery, WAF protection, API routing, or bot management can become unreachable within seconds regardless of how healthy their AWS infrastructure is behind the scenes.
Why AI Chatbots Are Transforming Customer Engagement
Modern websites and digital services demand speed, personalization, and frictionless engagement. With users expecting instant answers and tailored experiences, the true competitive advantage lies not in flashy design or static FAQs, but in deep contextual insights and functionality with tools like Deep Research and functional agents.

How Can You Modernize Your Cloud for the AI Era?
Modernizing your cloud infrastructure goes beyond mere migration; it's about establishing a robust foundation for AI-driven intelligence and streamlined operations. For small businesses and startups, redesigning this infrastructure can unlock a world of possibilities, including predictive insights, enhanced automation, and impressive scalability.
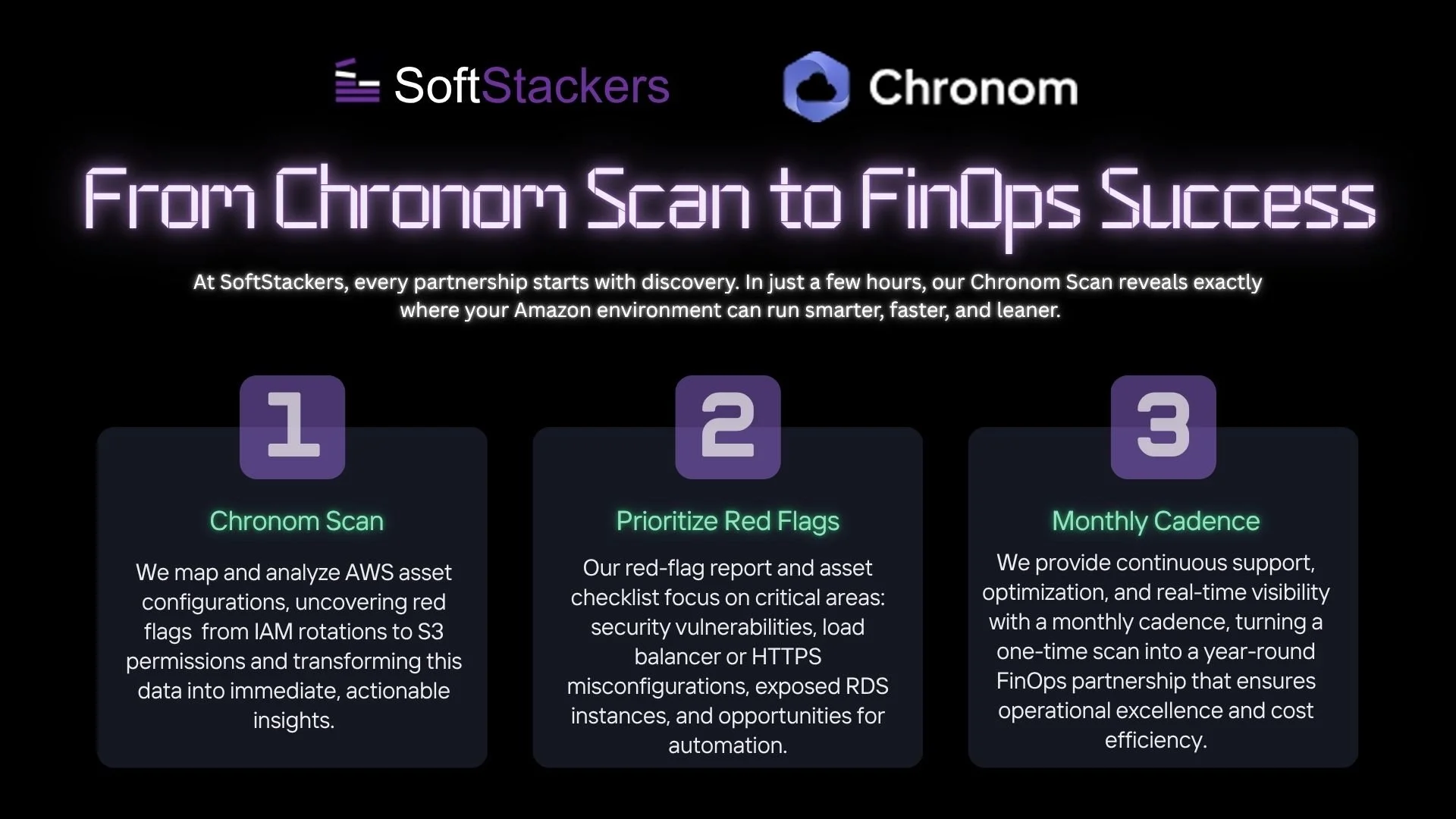
How a 5-Minute Chronom Scan Becomes a Year-Round FinOps Partnership
Even in today's rapidly evolving cloud environment, the fundamentals of Amazon environment administration remain crucial. It's easy to be sidetracked by new features or assume all is well because your application is running, but this is precisely when returning to the basics becomes essential.

Reid Hoffman’s Vision: How AI Can Help Transform Healthcare From Cancer Research to Real-World Innovation
“AI was a mechanism to scale‑vastly the kinds of work that we were doing in any one laboratory, and across diseases.” Reid Hoffman, (Business Insider, 2024)
When Reid Hoffman, the visionary founder of LinkedIn, speaks about innovation, the world listens.

Holiday AI Readiness Checklist to Prevent Outages and Capture Traffic
The recent Amazon outage is a clear indicator that even major cloud providers are susceptible to downtime, causing widespread disruptions. This serves as a critical warning for startups, retailers, and SaaS teams: systems unprepared for surges in AI-driven traffic are vulnerable. With Adobe forecasting a 520% increase in AI-driven holiday traffic, it's imperative to assess the readiness of your current infrastructure.

What Is Agentic AI as a Retail Primer
Retail competition is fierce and it’s only getting MORE competitive. With modern retailers like Amazon.com and Shein, retailers have to modernize and automate like the large retailers but struggle with internal resources and with decision making on what technologies to adopt.

What Amazon Quick Suite Means for Retail CTOs
Amazon Quick Suite represents a major leap forward in agentic AI intelligent systems that don’t just automate tasks, but actively make and execute decisions within the boundaries of enterprise governance. Designed to run natively inside AWS, Amazon Quick Suite integrates seamlessly with over 1,000 enterprise applications, creating a secure, end-to-end automation layer for retail operations

How Mid-Market Retailers Achieve Amazon-Level Supply Chain Visibility Using AWS.
Amazon has set the gold standard for supply chain efficiency, leveraging advanced technologies to achieve unparalleled visibility and responsiveness. Many mid-market retailers might believe such sophisticated operations are out of reach, reserved only for companies with vast resources. However…

Synthetic Data and VLM Annotation
Synthetic Data and VLM Annotation
Synthetic Data Acquisition and Image Annotation and why we went another way.
